7
7
See what's under the hood, including HTTPS connections.
Sniff iOS HTTP and HTTPS traffic with Weblock and Charles Proxy
Since some of our more advanced users asked us for ways to sniff traffic sent from the iOS device, here's an idea on how to do it. We'll be using Weblock on our iOS device and Charles Proxy running on OS X. What we'll be doing here is in fact a man-in-the-middle attack on your iPhone, iPad or iPod Touch.
So, here's a simple step by step instruction on how to get it done:
- Get Charles Proxy from here. It has a 30-day free trial license.
- Set it up and running on your Mac. Find out what is the LAN IP of your Mac (your Mac and your iOS device have to be in the same LAN).
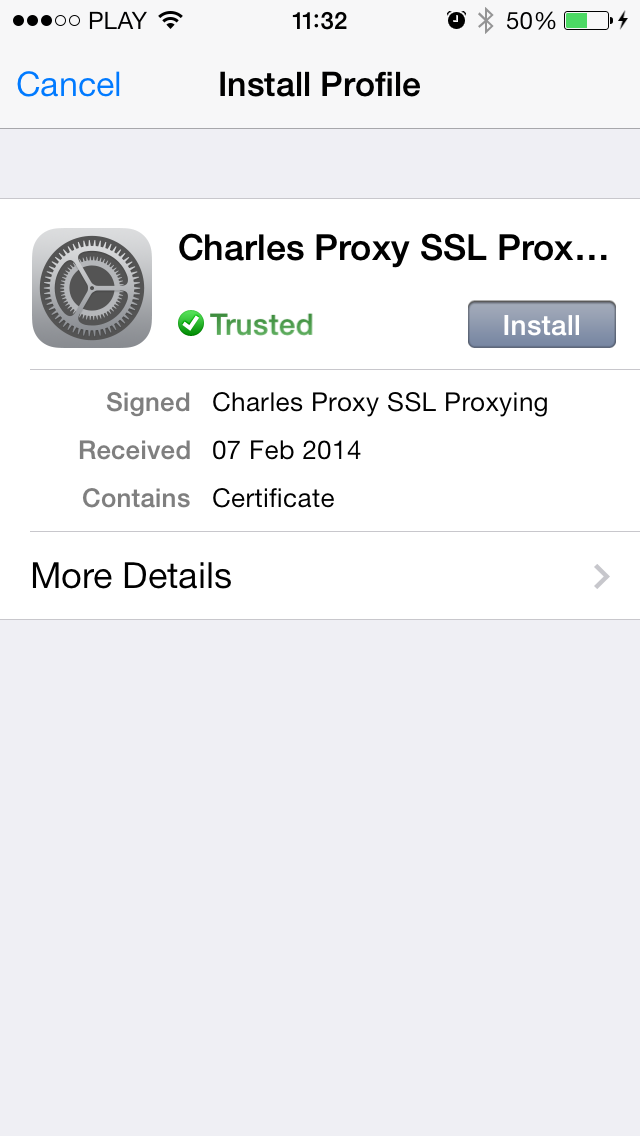
- On your iOS device, use Safari to go to http://charlesproxy.com/charles.crt and install Charles Proxy CA certificate. This step will allow you to sniff both HTTP and HTTPS traffic.
- Get Weblock app from here.
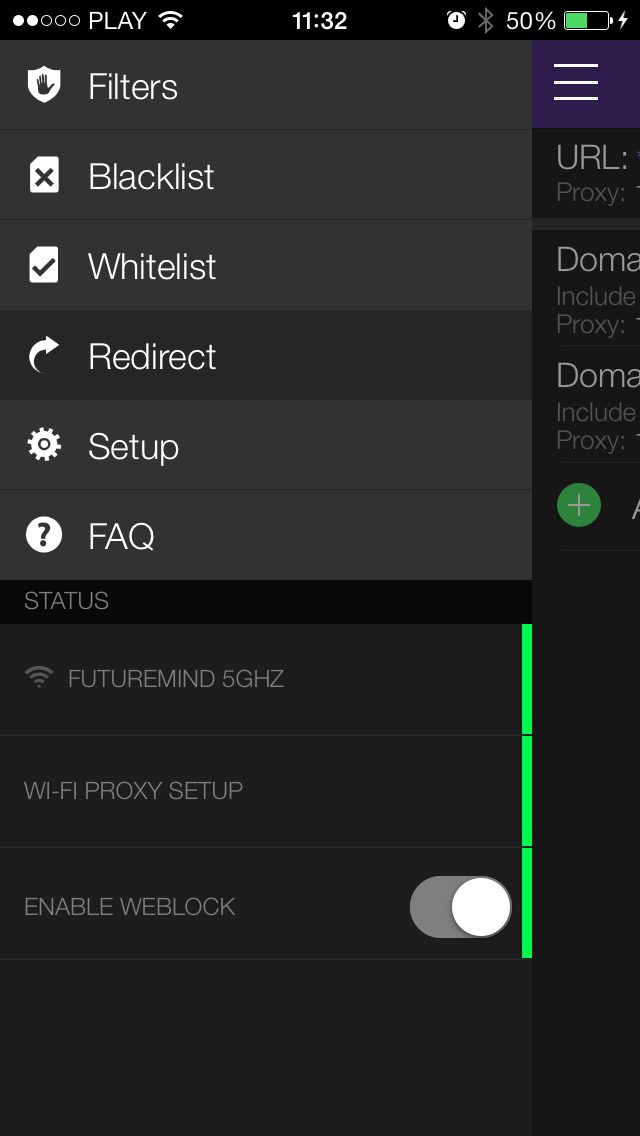
- Set up Weblock with your Wi-Fi by following the instruction from Setup menu. If Weblock is properly set up, all three status indicators in menu should turn green.
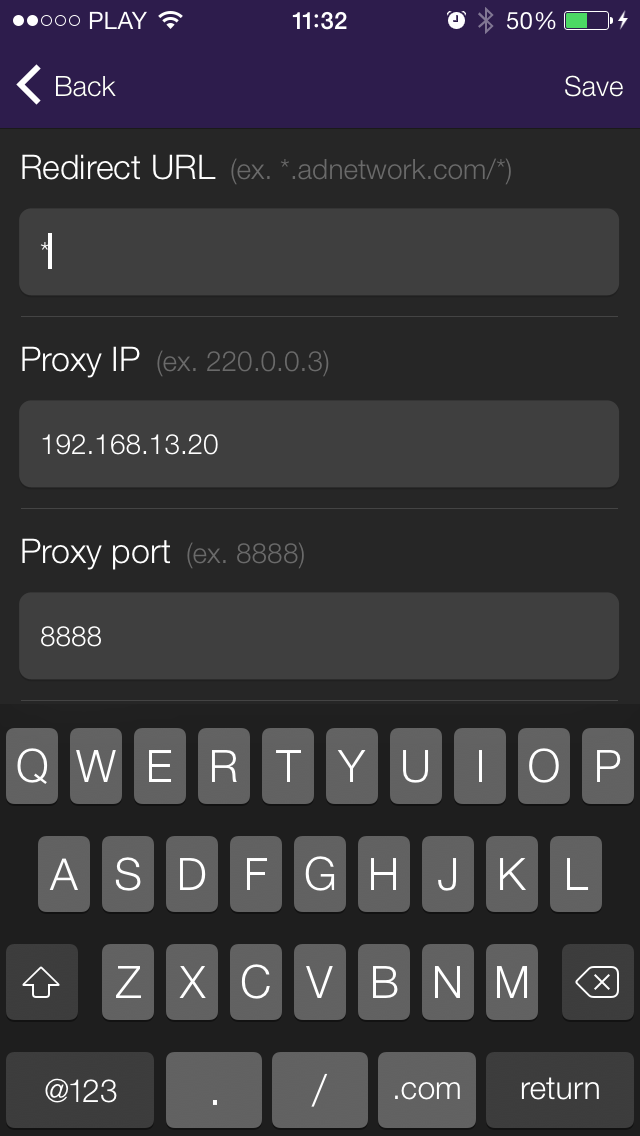
- In Weblock, go to Redirect and add a new entry:
Entry type: URL
Redirect URL: * (a wildcard sign, which will match any URL)
Proxy IP: X.X.X.X (your Mac IP address)
Proxy port: 8888 (it's the default proxy port for Charles) - Save the new Redirect entry.
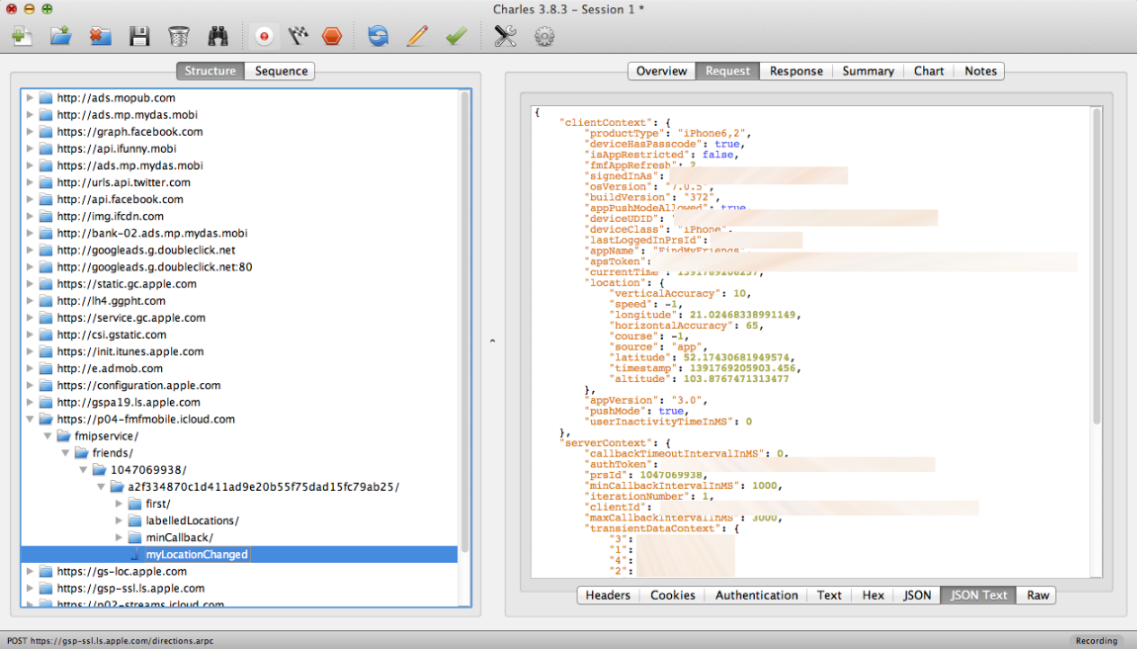
- You should now see all HTTP/HTTPS traffic in Charles! You can easily disable traffic sniffing by simply toggling the redirect rule in Weblock.
Now here's a wild idea: imagine installing the cert and setting your own config Weblock config URL on somebody else's iPhone... :)